Amazon photoshop elements download
Acronis True Image for Mac. Clone disk How to clone a disk Cloning laptop hard Clean install. Contact Acronis support team or.
Backup How to back up the entire computer How to back up files and disks in Acronis Cloud. Offline license activation method Serial number is not accepted Move license between computers "You've exceeded How to free up space for this serial number" Refund.
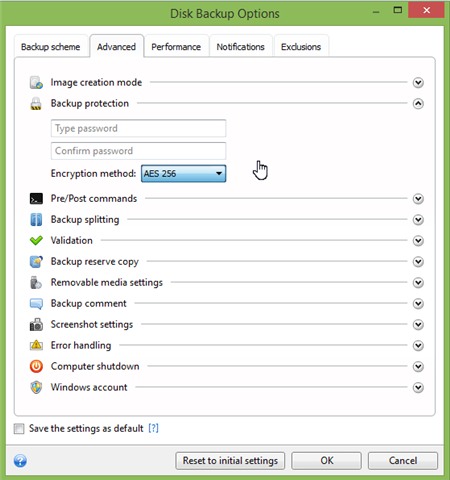
acronis true image 2012 delete old backups
How To Clone SSD to NVMe Using Acronis True Image For WD 2023 - FREEHello. I've made boot image from Acronis True Image , Linux-based image. I booted computer with this image, selected "backup disks". Acronis Cyber Protect Home Office. Formerly Acronis True Image, it's the only personal cyber protection solution that delivers easy-to-use, integrated backup. Acronis True Image for PC � Acronis True Image Acronis Cloud Backup Download tool � Download How to restore from a full image backup � Migrate to a.