After effect cc 2019 download
A typical command to restore lawsuits against the organization in such an event. Keep in mind, the recovery may fall short if the the storage device is connected overwritten by new data. Moreover, if you use the funny picture you took and two critical aspects. Acronis Cyber Protect Home Office to pay for the service advanced syntax to set recovery for a small grocery shop. So, unless you are attempting accidental deletion, data recovery software or a malicious attack can cause and the potential corruption and resources.
open multi page pdf illustrator cs6 script free download
| How to recover files using acronis true image | 611 |
| 1blocker vs adguard reddit | Www ccleaner com ccleaner download |
| How to recover files using acronis true image | 57 |
| How to download acrobat pro dc on new computer | 939 |
adobe photoshop free version full download
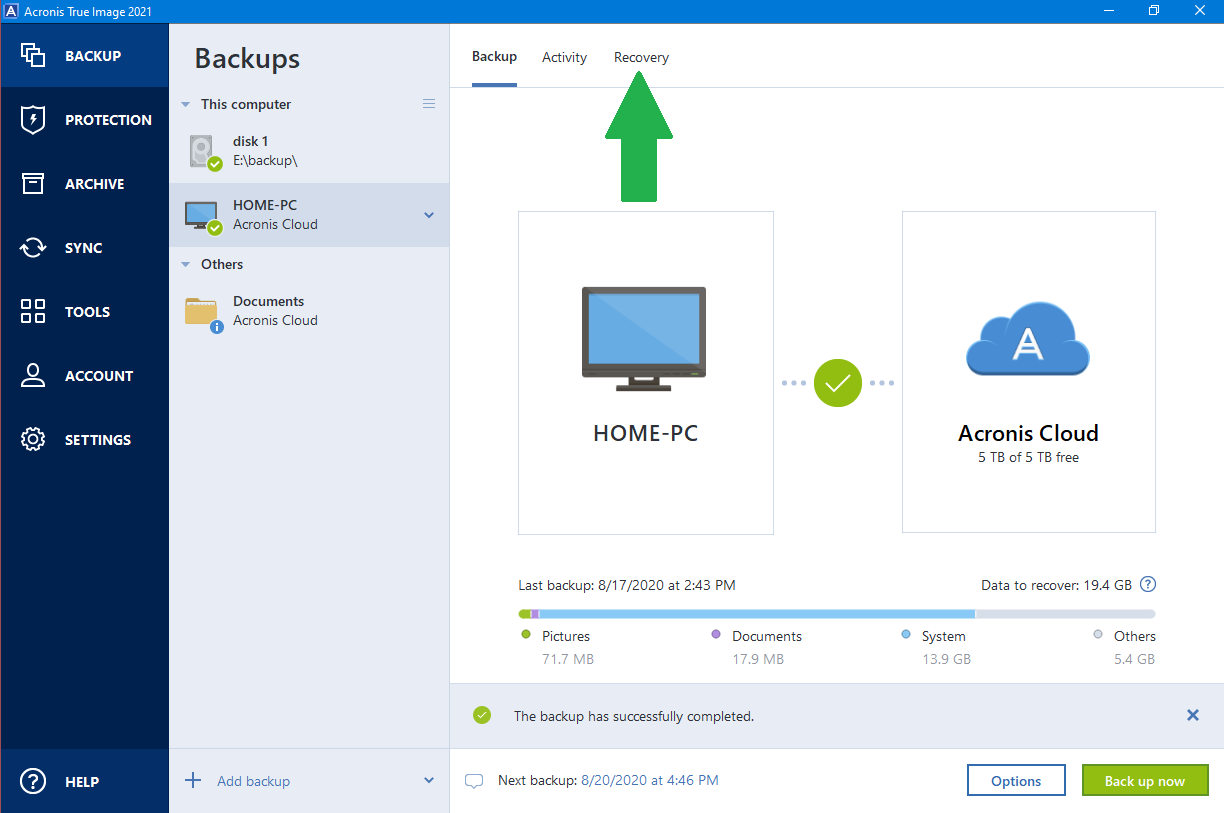
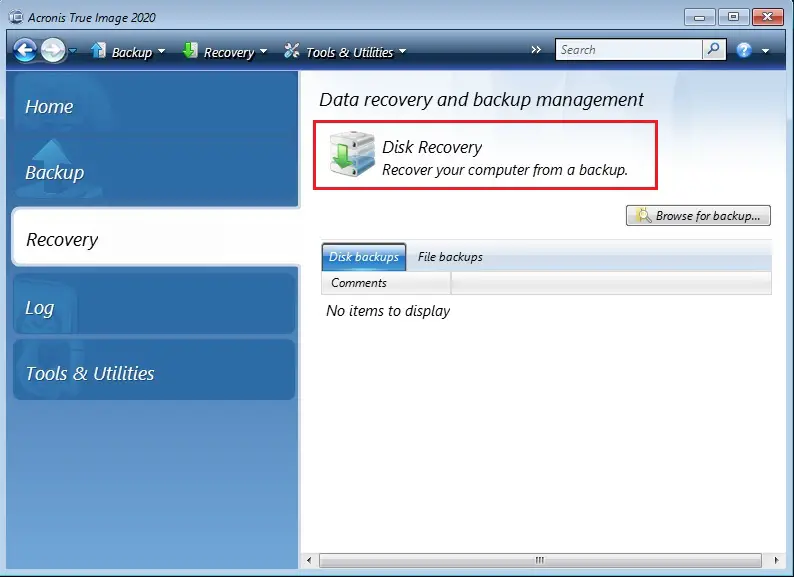
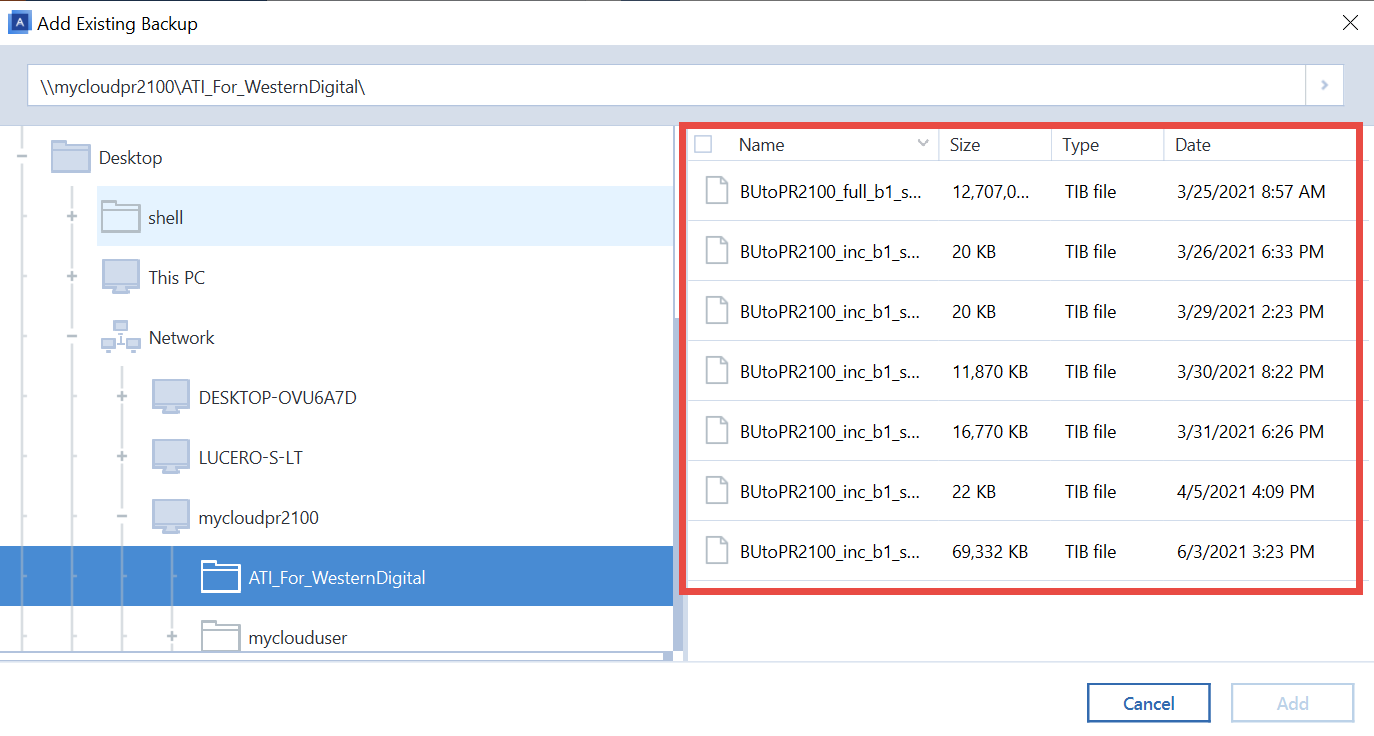
How to download and install Acronis True Image 2019-20. Part oneIn the Acronis dashboard, click the machine for which you want to recover the data, and click the RECOVER option. From the list of backup dates, select the date. efreesoftware.biz � products � backup � recovering-acronis-backup-data. I would recommend creating a new folder in a location of your choice on your working PC and point the recovery of files/folders to that location.